20+ firewall network diagram
Azure Firewall is a highly available managed firewall service that filters network and application level traffic. It contains the cluster requirements for a base AKS deployment and additional requirements for optional addons and features.
The Proposed Wireless Lan Network With 20 Workstations Download Scientific Diagram
If you specify a protocol and a port range the firewall rule applies to that destination port range for the protocol.

. Distributions include the Linux kernel and supporting system software and libraries many of which are provided. The big red circle represents the virtual adapter to which NAT. The resource records contained in the DNS associate domain names with other forms of information.
Linux is typically packaged as a Linux distribution. In the following diagram the network load balancer directs traffic to the middle node and the traffic is redirected to a Pod on the first node. Resource server The server hosting the protected resources capable of accepting and responding to protected resource requests using access tokens.
The common at home setup for pfSense is shown below I even included the XBox One which initially showed STRICT NAT. The benefits of a VPN include increases in functionality security and management of the private networkIt provides access to resources. A virtual private network VPN extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
This article provides the necessary details that allow you to secure outbound traffic from your Azure Kubernetes Service AKS. Since 1992 Samba has provided secure stable and fast file and print services for all clients using the SMBCIFS protocol such as all versions of DOS and Windows OS2 Linux and many others. RAID 0 RAID 1 RAID 5 RAID 10 also known as RAID 10 This article explains the main difference between these raid levels along with an easy to understand diagram.
Azure Firewall is priced in two ways. ASCII characters only characters found on a standard US keyboard. The following diagram illustrates some examples where firewall rules can control ingress connections.
1 125hour of deployment regardless of scale and 2 0016GB of data processed. Samba is the standard Windows interoperability suite of programs for Linux and Unix. Computing is any goal-oriented activity requiring benefiting from or creating computing machineryIt includes the study and experimentation of algorithmic processes and development of both hardware and softwareComputing has scientific engineering mathematical technological and social aspects.
You may see numerous PORT commands. 192168209 is a member server and STA Collector will be installed on it. IP addresses VLAN IDs and subnet masks.
Logical Network Diagrams Explained. Then the user will be displayed on Sophos Firewall as STAS live user. Must contain at least 4 different symbols.
Please enter the name by which you would like to log-in and be known on this site. On most situations you will be using one of the following four levels of RAIDs. It has the ability to process traffic across subscriptions and VNets that are deployed in a hub-spoke model.
It is often abbreviated as PM. These are most commonly used to map human-friendly domain names to the numerical IP. In this post well take a look at what a logical network diagram is.
To share files through Samba see Server section. Simple causal reasoning about a feedback system is difficult because the first system influences the. Introduction of Firewall in Computer Network.
The EdgeRouter uses a stateful firewall which means the router firewall rules can match on different connection states. For a large network it is a hectic task for administrators to manually add each route for the network in the routing table on each router. In this article.
RAID stands for Redundant Array of Inexpensive Independent Disks. Having played with it and using it right now. All instances in the network.
In this diagram youll see the pfSense firewall as a. A hardware firewall is a device that is connected to the network and filters the packets based on a set of rules. A firewall can exist as hardware or software or both.
Linux ˈ l iː n ʊ k s LEE-nuuks or ˈ l ɪ n ʊ k s LIN-uuks is an open-source Unix-like operating system based on the Linux kernel an operating system kernel first released on September 17 1991 by Linus Torvalds. Red Hat JBoss Operations Network a key component of the Red Hat JBoss managed offerings provides built-in management and monitoring capabilities to effectively administer all of your Red Hat JBoss application environments helping you improve operational efficiency reduce costs and ensure a positive experience for your end users. The network load balancer is aware of all nodes in your cluster and configures your VPC networks firewall.
In a logical diagram youll generally visualize the following elements in your logical network topology. Diagram of a network configuration with firewalls a router and a DMZ. 192168205 is AD DC and STA Agent will be installed on it.
Firewalls are another method that an organization can use for increasing security on its network. Major computing disciplines include computer engineering. An intrusion detection system IDS.
Project management is the discipline of using established principles procedures and policies to manage a project from conception through completion. A logical network diagram depicts how information in the network flows. IANA states that this range should be between 49152 through 65535 but most likely youll see your application using a port just above 1024 -- the area that used to be the dynamic port number area.
In this diagram the vertical line next to the firewall represents the production network and you can see that 19216811 is the IP address of the companys firewall that connects them to the Internet. There is also a virtual host with three virtual machines running inside it. When the resource owner is a person it is referred to as an end-user.
The system can then be said to feed back into itself. 6 to 30 characters long. To access files shared through Samba on other.
Firewall policies are used to allow traffic in one direction and block it in another direction. The Domain Name System DNS is the hierarchical and decentralized naming system used to identify computers reachable through the Internet or other Internet Protocol IP networks. PfSense is one of the most used open source firewalls which runs on its own dedicated hardware.
7 in diagram logontype1png User detected in such way is known as STAS logon type 1. Resource owner An entity capable of granting access to a protected resource. In the example diagram above firewall rules will be added to limit the traffic between the trust LAN 1921681024 and the GUEST.
RFC 6749 OAuth 20 October 2012 11Roles OAuth defines four roles. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management SIEM system. The firewall rule applies to all instances in the network.
Feedback occurs when outputs of a system are routed back as inputs as part of a chain of cause-and-effect that forms a circuit or loop. Typically in a packet trace of active mode FTP youll see the data channel originating from server port 20 to a dynamic client port number. 300 in free credits and 20 free products.
Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy violations. The notion of cause-and-effect has to be handled carefully when applied to feedback systems.

Next Generation Firewall Images From Palo Alto Cisco Sonicwall Computer Security Palo Alto Firewall Generation

Topology Parallel Firewall Integrated With Nlb For Incoming Traffic Download Scientific Diagram

A Multi Cluster Shared Services Architecture With Amazon Eks Using Cilium Clustermesh Containers

Extending The Zero Trust Architecture Concept To Apis Vmware Security Blog Vmware

Pci Dss Baseline For Anthos Clusters On Vmware Gke On Prem Cloud Architecture Center Google Cloud
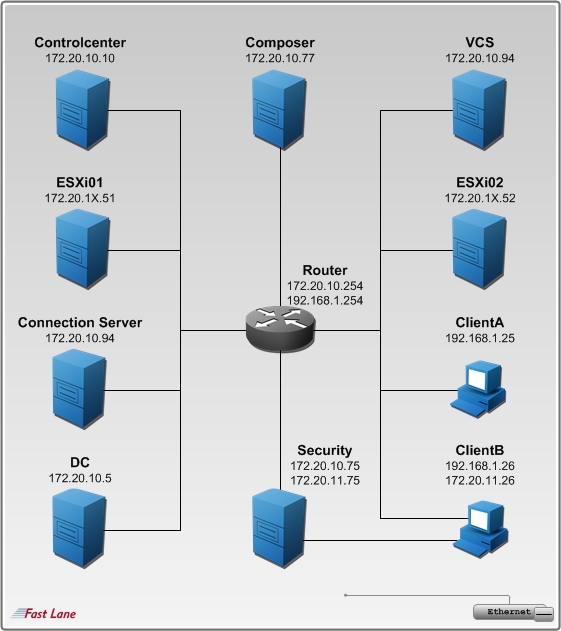
Remote Labs
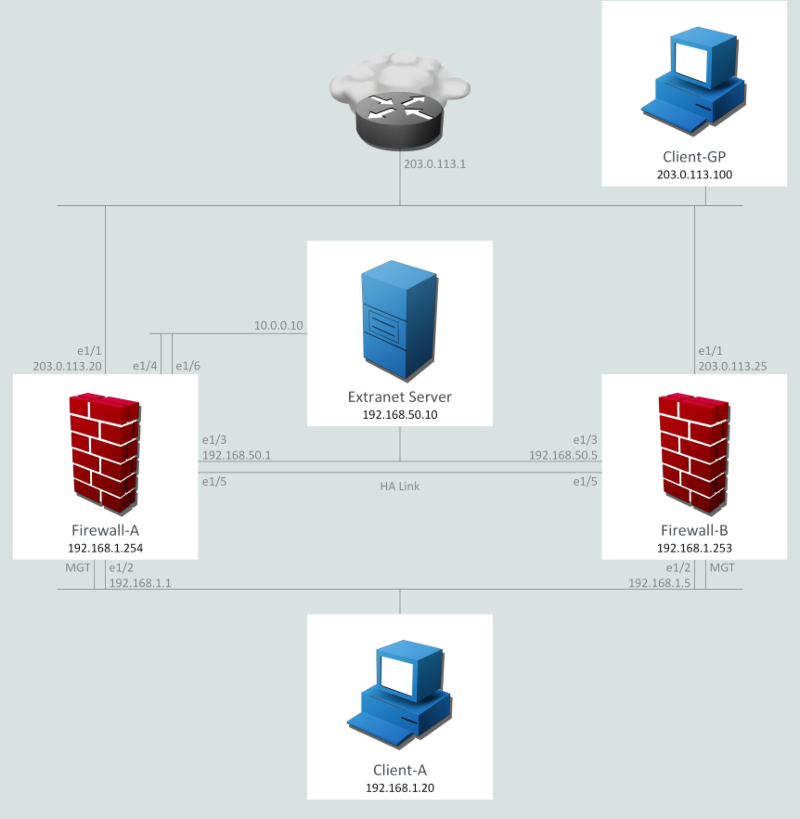
Palo Alto Firewall Essentials Configuration And Management

Illustration Of The Proposed Framework With 20 Mv Cameras Download Scientific Diagram
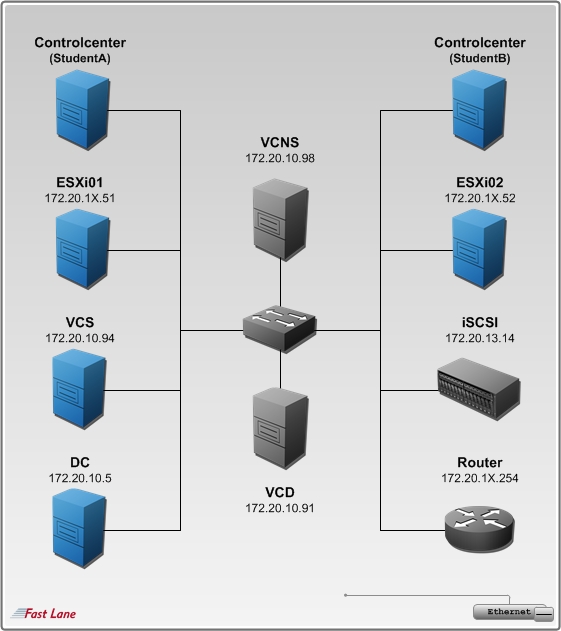
Remote Labs

Installation Guidelines Octopus Deploy

Reverse Http 20 Can Make A Wot Device Situated Behind A Firewall Nat Download Scientific Diagram
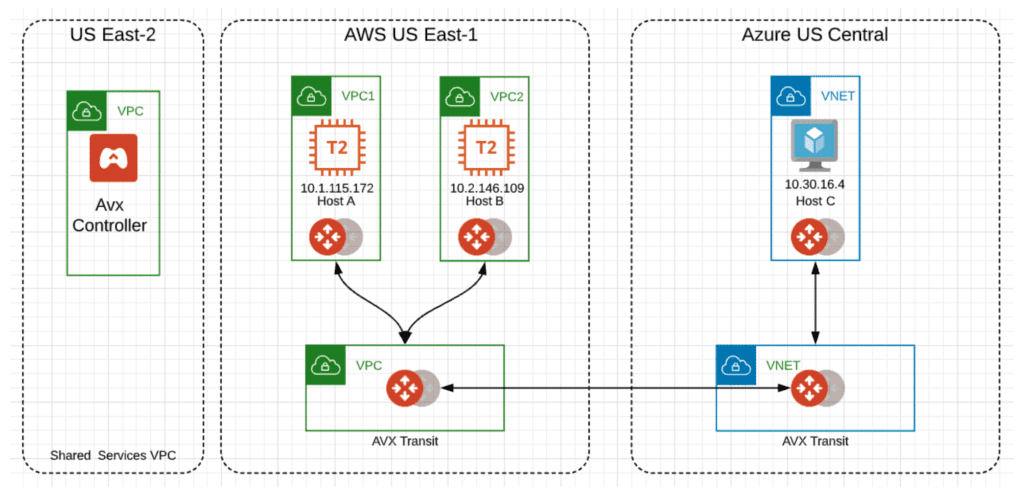
Accelerate Cloud Network Troubleshooting To Minimize Network Downtime With Aviatrix Multi Cloud Flightpath Aviatrix

Bundled Load Balancing With Seesaw Anthos Clusters On Vmware Google Cloud

A Dcell 1 Network When N 3 20 Download Scientific Diagram

Topology Parallel Firewall Integrated With Nlb For Outgoing Traffic Download Scientific Diagram

Libraries For Draw Io Contribute To Jgraph Drawio Libs Development By Creating An Account On Github Flow Chart Create Mind Map Org Chart

Council B S Current Email Network Diagram Fig 4 Council C S Current Download Scientific Diagram